Check Point IPS update in response to Superfish
You may have heard about the recent Superfish SSL Adware and how it compromises the security of Lenovo laptops. The good news is that Check Point have now updated their IPS signature definition to detect and block any SSL session secured with this certificate. This recent update to their IPS (Intrusion Prevention System), once installed on your gateway, will give you instant protection against any web-based communication secured by Superfish until the software can be removed from the laptop.
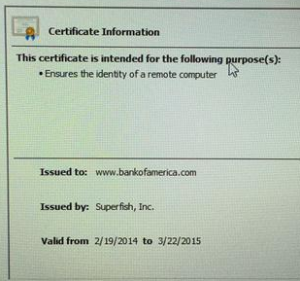
To recap, the Superfish is an Ad injecting software installed onto Lenovo laptops. The idea of the program was to target ads towards the consumer, based on the websites they were visiting. The program does this by intercepting all web based communication and passing it through their inspection engine in order to extract and pass back a result. The problem comes from the fact that HTTPS communication has to be encrypted from the source to the destination in order to keep the data secure and private. Superfish gets around this problem by essentially mimicking the same function as an attacker would and becoming a “man-in-the-middle.” The SSL communication from the web server is terminated with the Superfish program and then creates a new SSL connection between itself and the browser, presenting the web page back to you. If you were to check the SSL certificate from a website on a Lenovo laptop, installed with Superfish, you would see the certificate is signed by Superfish.
Intercepting an SSL session poses security risks because hackers can use the same process to steal information such as credit card details and personal information unbeknownst to the end user. As the software and root certificate/private key to perform this function is already installed on several laptops, it would make it easier for an attacker to attempt an exploit.
Lenovo have issued an advisory on Thursday 19th February 2015 and a automated tool earlier today on how to help users remove the software and certificate.
Network Security Recommendations
Liaising with our network security vendors, we discuss your network's vulnerabilities and compile a report which includes observations from our site assessment, as well as a set of recommendations specificially designed to protect your network going forward.
Network Switching
Network switches are the backbone of any IT infrastructure. We've partnered with Cisco to deliver a strategic advantage to your network. Cisco switching solutions can be customised according to your exact technical and budgetary needs. For more information please contact our technical sales team to discuss further.
Wireless Networks
We’ve got a depth of experience in providing enterprise-class wireless networks. Partnering with Cisco, Meraki and Aruba Networks, we offer and deliver unified and robust wireless networks - all of which have easy-to-deploy/use centralised management systems. If you are considering upgrading or deploying a wireless solution in your organisation, use our contact form to get in touch.
Security Audits
Security starts with an audit on your existing infrastructure. We perform a full health check, including firewall rule configuration and packet capture, to review all traffic flowing through the internet gateway. This work includes a botnet scan and any EOL vulnerabilities.