Check Point IPS update in response to Superfish
You may have heard about the recent Superfish SSL Adware and how it compromises the security of Lenovo laptops. The good news is that Check Point have now updated their IPS signature definition to detect and block any SSL session secured with this certificate. This recent update to their IPS (Intrusion Prevention System), once installed on your gateway, will give you instant protection against any web-based communication secured by Superfish until the software can be removed from the laptop.
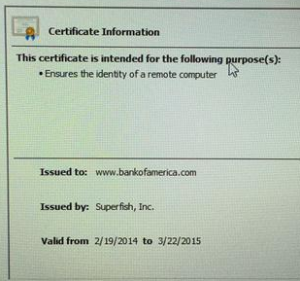
To recap, the Superfish is an Ad injecting software installed onto Lenovo laptops. The idea of the program was to target ads towards the consumer, based on the websites they were visiting. The program does this by intercepting all web based communication and passing it through their inspection engine in order to extract and pass back a result. The problem comes from the fact that HTTPS communication has to be encrypted from the source to the destination in order to keep the data secure and private. Superfish gets around this problem by essentially mimicking the same function as an attacker would and becoming a “man-in-the-middle.” The SSL communication from the web server is terminated with the Superfish program and then creates a new SSL connection between itself and the browser, presenting the web page back to you. If you were to check the SSL certificate from a website on a Lenovo laptop, installed with Superfish, you would see the certificate is signed by Superfish.
Intercepting an SSL session poses security risks because hackers can use the same process to steal information such as credit card details and personal information unbeknownst to the end user. As the software and root certificate/private key to perform this function is already installed on several laptops, it would make it easier for an attacker to attempt an exploit.
Lenovo have issued an advisory on Thursday 19th February 2015 and a automated tool earlier today on how to help users remove the software and certificate.
IT Equipment Removal
Our office move team will dovetail all activity with your own plans - ensuring that your network is running right up to the last minute; providing interim network services wherever possible. We ensure that all works are carried out efficiently and painlessly - stripping all reusable network equipment before reinstalling it in your new space. We believe in equipment sustainability wherever possible. As such, we carefully consider what equipment is still fit for purpose within your new network environment - managing the heavy lifting element to this part of the office move process.
Infrastructure & Hosting
We deliver reliable and robust infrastructure and hosting. Our technical team can help design your network, or alternatively we have our own resilient Data Centre, where we can fully manage your hosted solution. Whatever your needs, we will accommodate them.
Borderless Networks
Workspace, as we know it, has changed dramatically in recent years. We can assist in the design and delivery of your borderless network, working with our partner Cisco. Our aim is to enable various services such as mobility, security and applications with our key vendor technologies, whilst simplifying operations, increasing productivity, and aiding the operational efficiency of your organisation.
Virtual Office Numbers
We provide UK & EMEA virtual office numbers that allow you to have a virtual presence in a region of your choice. Depending on location, we can provide toll-free numbers. We can route all numbers to any UK landline, UK mobile – or indeed any number worldwide.